Cracking The Code: A Deep Dive Into Format-Preserving Encryption
Alright, let's get down to business. If you're reading this, chances are you've stumbled upon one of the most fascinating yet underappreciated concepts in the world of cybersecurity: format-preserving encryption. Now, before your eyes glaze over, let me tell you something cool. This isn’t just another buzzword in the tech world; it’s a game-changer when it comes to protecting sensitive data while keeping it usable. So buckle up, because we're about to unravel the mysteries behind this tech marvel. And trust me, by the end of this, you'll be a total FPE pro.
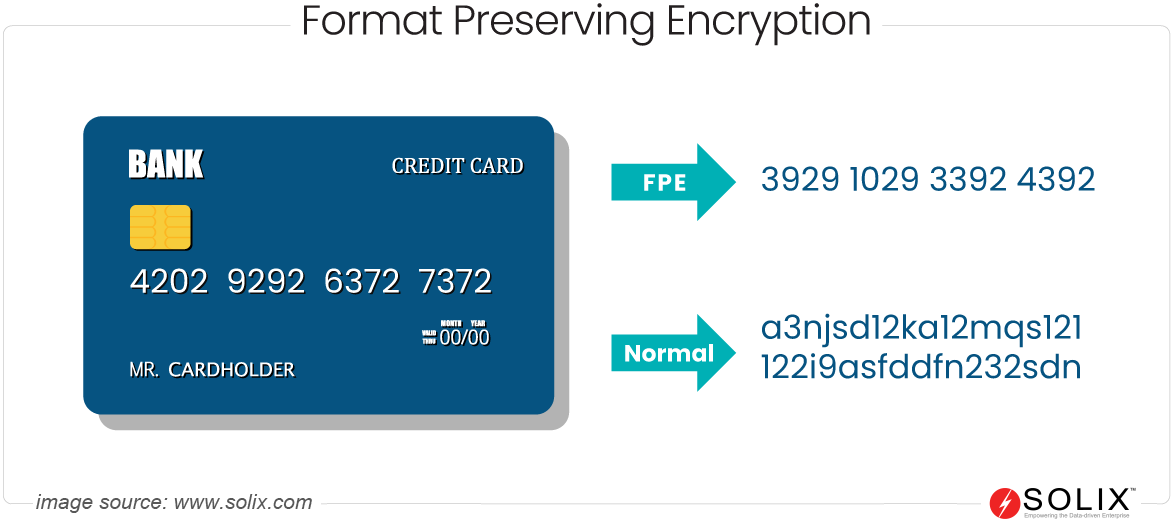
In today's digital age, data security is more important than ever. Cybercriminals are getting smarter, and traditional encryption methods just don’t cut it anymore. Enter format-preserving encryption, or FPE for short. This nifty little tool allows you to encrypt data without changing its original format. Imagine encrypting a credit card number while keeping it as a 16-digit number. Sounds like magic, right? Well, it's not—it's science. And we’re diving headfirst into the science behind it.
Now, why should you care about format-preserving encryption? Because it’s not just about security; it’s about efficiency and usability too. Traditional encryption methods can be cumbersome, especially when dealing with legacy systems or applications that expect data in a specific format. FPE solves this problem by ensuring that encrypted data looks and behaves like the original data. It’s like having your cake and eating it too—or in tech terms, securing your data without breaking your system. So, let’s dive in and explore the ins and outs of this awesome technology.
Read also:Is Noah Galvin Trans Exploring The Facts And Clearing Up The Confusion
What Exactly is Format-Preserving Encryption?
Let’s start with the basics. Format-preserving encryption, or FPE, is a cryptographic technique designed to encrypt data while preserving its original format. Unlike traditional encryption methods that transform data into an unreadable format, FPE ensures that the encrypted output matches the structure of the original input. For instance, if you encrypt a 10-digit phone number, the result will still be a 10-digit number. This makes FPE particularly useful in scenarios where data format matters, such as credit card numbers, social security numbers, or even dates.
Here’s the kicker: FPE doesn’t just preserve the format; it also ensures that the data remains secure. By using advanced algorithms, FPE transforms sensitive data into something unreadable to unauthorized users while maintaining its usability for authorized systems. This dual functionality is what sets FPE apart from other encryption methods. And let’s be honest, in today’s world, we need all the security we can get.
Why Does Format-Preserving Encryption Matter?
In a world where data breaches are becoming increasingly common, the importance of format-preserving encryption cannot be overstated. Traditional encryption methods often require significant changes to existing systems, which can be costly and time-consuming. FPE eliminates this problem by allowing organizations to encrypt data without disrupting their current infrastructure. This means businesses can enhance their security posture without sacrificing performance or compatibility.
But that’s not all. FPE also plays a crucial role in compliance with data protection regulations. Many industries, such as finance and healthcare, are subject to strict regulations that mandate the protection of sensitive data. By using FPE, organizations can meet these requirements while ensuring that their data remains functional within existing systems. It’s like having a security blanket that keeps you warm and cozy while also being practical.
Key Benefits of Format-Preserving Encryption
Let’s break it down. Here are some of the key benefits of using format-preserving encryption:
- Preserves Data Format: Encrypted data retains its original structure, making it easier to integrate with existing systems.
- Enhances Security: FPE uses advanced algorithms to ensure that sensitive data is protected from unauthorized access.
- Improves Compliance: By maintaining data usability, FPE helps organizations meet regulatory requirements without compromising security.
- Reduces Costs: Since FPE doesn’t require significant changes to existing systems, it can save businesses time and money.
How Does Format-Preserving Encryption Work?
Now that we’ve covered the what and why, let’s talk about the how. FPE works by using a combination of encryption algorithms and domain-specific rules to transform data while preserving its format. The process typically involves the following steps:
Read also:Cristina Carmella Onlyfans A Rising Star In The Digital Age
First, the data is divided into smaller segments based on its format. For example, a credit card number might be split into individual digits or groups of digits. Next, each segment is encrypted using a cryptographic algorithm, such as AES or Feistel networks. Finally, the encrypted segments are reassembled to form the final output, which matches the original format of the input data.
One of the most common algorithms used in FPE is the Feistel network, which is a structure used in symmetric key block ciphers. This algorithm works by dividing the input data into two halves and applying a series of rounds of encryption to each half. The result is a secure and format-preserving output that can be easily integrated into existing systems.
Common Algorithms Used in FPE
Here are some of the most commonly used algorithms in format-preserving encryption:
- AES: Advanced Encryption Standard is a widely used encryption algorithm that can be adapted for FPE.
- Feistel Networks: A structure used in symmetric key block ciphers, Feistel networks are particularly well-suited for FPE due to their ability to preserve data format.
- FFX Mode: Developed by NIST, the FFX mode is a specialized encryption mode designed specifically for FPE.
Applications of Format-Preserving Encryption
So, where can you use format-preserving encryption? The answer is: almost anywhere. FPE is particularly useful in industries that deal with sensitive data, such as finance, healthcare, and e-commerce. Here are some of the most common applications:
In the financial sector, FPE is used to protect credit card numbers, bank account numbers, and other financial data. By encrypting this data while preserving its format, businesses can ensure that their systems remain functional while maintaining compliance with regulations like PCI DSS.
In healthcare, FPE is used to secure patient data, such as social security numbers and medical record numbers. This helps organizations meet the requirements of regulations like HIPAA while ensuring that their data remains usable within existing systems.
Real-World Examples of FPE in Action
Let’s take a look at some real-world examples of format-preserving encryption in action:
- Payment Processing: Many payment processors use FPE to encrypt credit card numbers while maintaining their original format. This allows them to process payments securely without disrupting their existing systems.
- Healthcare Systems: Hospitals and clinics use FPE to secure patient data while ensuring that it remains accessible to authorized users. This helps them meet regulatory requirements while maintaining operational efficiency.
Challenges and Limitations of Format-Preserving Encryption
Of course, no technology is perfect, and FPE is no exception. While it offers many benefits, there are also some challenges and limitations to consider. One of the biggest challenges is performance. Since FPE involves complex algorithms, it can be slower than traditional encryption methods. This can be a problem in high-throughput environments where speed is critical.
Another limitation is compatibility. While FPE is designed to work with existing systems, it may not be compatible with all legacy systems. This can require additional development work to ensure that FPE can be integrated seamlessly into existing infrastructure.
Overcoming the Challenges
Despite these challenges, there are ways to overcome them. For example, advancements in hardware acceleration and parallel processing can help improve the performance of FPE. Additionally, many vendors offer pre-built solutions that are optimized for specific use cases, making it easier to implement FPE in existing systems.
Best Practices for Implementing Format-Preserving Encryption
If you’re considering implementing FPE in your organization, here are some best practices to keep in mind:
- Start Small: Begin by implementing FPE in a small, controlled environment to test its effectiveness and compatibility.
- Choose the Right Algorithm: Select an algorithm that is appropriate for your specific use case and data format.
- Monitor Performance: Keep an eye on system performance to ensure that FPE doesn’t negatively impact your operations.
Future Trends in Format-Preserving Encryption
As technology continues to evolve, so too will the field of format-preserving encryption. One of the most exciting developments is the rise of quantum computing, which has the potential to revolutionize the way we approach encryption. While quantum computing poses a threat to traditional encryption methods, it also offers new opportunities for developing more secure and efficient encryption algorithms.
Another trend to watch is the increasing use of AI and machine learning in encryption. These technologies can help improve the performance and effectiveness of FPE by automating many of the complex processes involved in encryption and decryption.
What’s Next for FPE?
Looking ahead, the future of format-preserving encryption looks bright. As more organizations recognize the importance of data security and usability, the demand for FPE is likely to increase. This will drive innovation and lead to the development of even more advanced and efficient encryption methods.
Conclusion
Well, there you have it. Format-preserving encryption is a powerful tool that offers a unique combination of security and usability. By preserving the format of sensitive data while ensuring its protection, FPE provides a practical solution for organizations looking to enhance their security posture without disrupting their existing systems. Whether you’re in finance, healthcare, or any other industry that deals with sensitive data, FPE is definitely worth considering.
So, what are you waiting for? Dive into the world of FPE and see how it can transform the way you approach data security. And don’t forget to share your thoughts in the comments below or check out some of our other articles for more insights into the world of cybersecurity.
Table of Contents
- What Exactly is Format-Preserving Encryption?
- Why Does Format-Preserving Encryption Matter?
- How Does Format-Preserving Encryption Work?
- Applications of Format-Preserving Encryption
- Challenges and Limitations of Format-Preserving Encryption
- Best Practices for Implementing Format-Preserving Encryption
- Future Trends in Format-Preserving Encryption
- Conclusion
Article Recommendations